Conficker worm on its pursuit updates itself !
Conficker B++, evil twin of Conficker, also known as W32/Conficker.worm, Downup, W32.Downadup and Kido, is a worm that takes advantage of Windows security vulnerability called MS08-067 in order to spread itself across networks. Once infected, Conficker may disable Windows system services such as Windows Defender, Automatic Backup, Windows Error Reporting, and Windows Automatic Update. Conficker could block certain security websites and may install further malware on your computer.
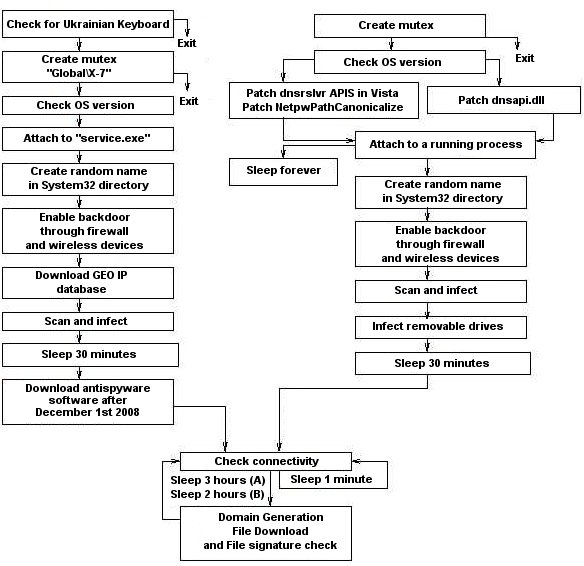
Conficker A (left) /B (right): Top-level control flow
Source : http://mtc.sri.com
Conficker B uses a different set of sites to query its external-facing IP address www.getmyip.org, www.whatsmyipaddress.com, www.whatismyip.org, checkip.dyndns.org. It does not download the fraudware Antivirus XP software that version A attempts to download. Conficker’s propagation methods vary among A and B.
Like Conficker A, after a relatively short initialization phase followed by a scan and infect stage, Conficker B proceeds to generate a daily list of domains to probe for the download of an additional payload.
A New Backdoor Service
Conficker B++ has added a new method for remote Win32 binary retrieval and execution. This new method entails the use a named pipe to receiving URLs from remote systems, retrieval of Win32 binaries using this URL, validation that the downloaded executable is properly signed by the Conficker authors, and immediate execution of the binary.
The new Conficker variant adds an extra function to the main thread if the OS is Windows XP, Windows 2000, or Windows 2003 Server
Conficker is known to block access to over 100 anti-virus and security websites.
OpenDNS, the free DNS service, plans to start blocking the Conficker worm’s attempts to connect to potential control servers using a predicted address list provided by Kaspersky. According to The Register, the new free service will also be able to alert administrators to the presence of the Conficker worm and assist them in locating infected machines.
Microsoft offers $250,000 reward for information leading to the arrest and conviction for the cybercriminals responsible for the fast spreading Conficker/Downadup worm.
Computer users who already have their Automatic Update feature turned on for Microsoft Windows Update may not be vulnerable to the Conficker worm. Upon detection of the Conficker worm, it is recommended that you configure your computer to receive critical updates and patches from Microsoft and run a full scan with an up-to-date version of your anti-virus or anti-malware program. Conficker may attempt to recreate itself on reboot.
![]()
Download Free Conficker Removal Tool
Joe Stewart from the Conficker Working Group has created an eye chart that allows for online identification of Conficker B and C infections. The idea is to load content from sites that are blocked by Conficker.
Check now http://www.confickerworkinggroup.org/infection_test/cfeyechart.html
If you can see all six images in both rows of the top table, you are either not infected by Conficker, or you may be using a proxy server, in which case you will not be able to use this test to make an accurate determination, since Conficker will be unable to block you from viewing the AV/security sites.
Possibly Related Posts:
- Speed up your Windows system with Autoruns, a free utility
- Track activities on Windows system with LastActivityView
- Process Monitor v3.2
- Prevent data loss: Monitor your hardrive’s health status with CrystalDiskInfo
- Hamsphere: Virtual Ham Radio transceiver on your PC
