Recover your Gmail and Orkut accounts from Bom Sabado attack
 Exploiting cross-site scripting flaw on Orkut, “Bom Sabado” worm is spreading like a plague on Orkut. Bom Sabado means ““Good Saturday” in Portuguese. It sends “Bom Sabado ” scraps to your friends and automatically joins your profile on some adult communities. It’s a cookie stealing script in action.
Exploiting cross-site scripting flaw on Orkut, “Bom Sabado” worm is spreading like a plague on Orkut. Bom Sabado means ““Good Saturday” in Portuguese. It sends “Bom Sabado ” scraps to your friends and automatically joins your profile on some adult communities. It’s a cookie stealing script in action.
Am I infected?
If you have seen “ Bom Sabado! “ scrap on orkut, on your scrapbook or your friends scrapbook, or seen this scrap on Gmail’s web interface, you are infected.
Don’t panic !
What should you do?
- Clear your cookies and cache.
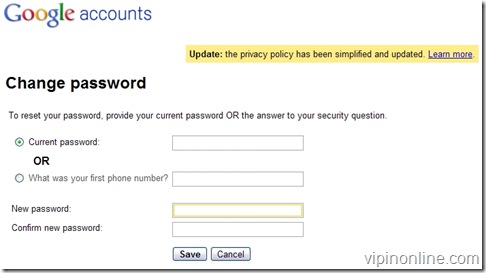
- Change your Google account password immediately by visiting the following link and don’t login to Orkut till Google engineers fix this issue.
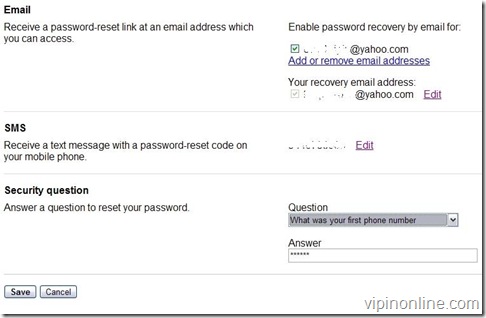
- Change the security question too
- Keep your Mobile phone no. updated for getting password reset code.
- Don’t try to open Orkut or messages from Orkut by e-mail. (SMTP & POP users may view the message in plain text)
- Stop visiting the scrapbooks of others till they fix this issue.
- How can you help to avoid its spreading?
- Login to mobile version of Orkut http://m.orkut.com from Opera Mobile and delete all “ Bom Sabado! “ scraps
Alternatively,
- Disable Javascript on your browser
- Login to mobile version http://m.orkut.com
Pass this information to your friends. Stay tuned for further updates.
Install and maintain an updated Anti-virus and Anti-Malware like, Malwarebytes Anti-Malware to keep your system free from Key loggers and backdoor trojans.
UPDATE from Google:
Hi all,
This is to inform you all that we’ve contained the “Bom Sabado” virus and have identified the bug that allowed this and have fixed it.
We’re currently working on restoring the affected profiles.
Thanks a ton to each of you who’s made an effort to alert everyone else about this.
Possibly Related Posts:
- Draw Diagrams online
- International Information Security Conference “c0c0n 2017” on August 18, 19 at Cochin, Kerala
- Kill-Switch for Petya ransomware on Windows
- International Information Security Conference “c0c0n 2016” on August 19, 20 at Kollam, Kerala
- 2GB of free Google Drive storage when you take your Security Checkup today